US Adoption Center Gladney Leaks Millions of Records Related to Adoptions Publicly
Almost 2 million entries with really sensitive information was exposed publicly for at least a week.
On April 7th 2025 while looking at some exposed databases on my logs, I noticed one with some really sensitive entries.
Upon further inspection, I noticed the logs were linked to a CRM that belonged to an Adoption Center in the United States, https://adoptionsbygladney.com and the server had been running with no authentication at least since April 1st.
The exposed data
The server contained a total of 1,930,615 records with around 5GB of data. Most of what I saw seemed to be related to Texas but it’s likely other states data was also present.
Each record contained a type. I couldn’t verify what most of the acronyms meant but the top 20 types of records were:
316326 Contacts 280884 Emails 273196 Leads 159209 spc10_contribution_payment 158076 spc14_Fund 157817 spc36_Acknowledgement_Card 148946 EPI_Family 81739 spc33_contribution_overview 60039 EPI_Pregnancy 50165 spc31_salutations 38829 EPI_Applications 29288 spc32_tribute_recipient 26249 EPI_Outreach 21554 Accounts 17328 GLD_Extended_Family_Or_HHM 13556 EPI_Birth_Information 13243 spc46_establishment 11274 spc30_soft_credit 10260 EPI_Birth_Fathers 9101 APAFI_AP_Adoption_File_Items
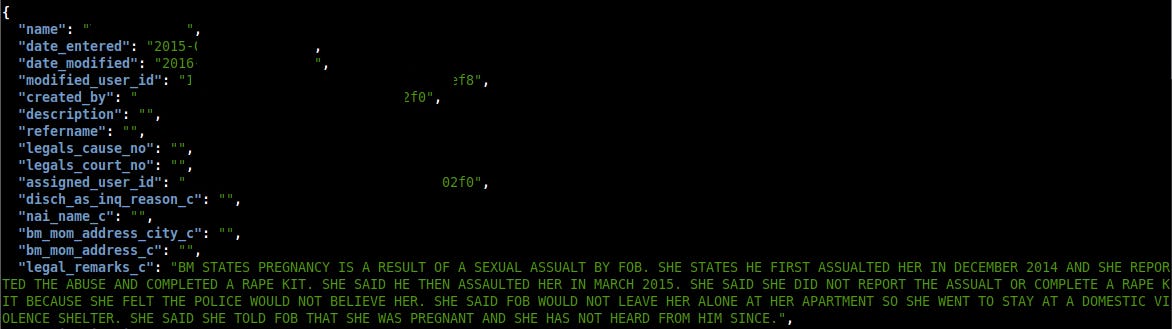
The amount of PII/PHI on each record varied and I’m not gonna detail everything but it contained information such as: contact details (name, email, address, phone), marriage and relationship information, birth information (DOB, state, name) and then information related to adoptions and birth parents.
It also contained fields for social security, drivers licence, passport and medicaid numbers. All the data was in plaintext, besides some passwords.
The data contained 219,163 unique email addresses.
Top 20 email domains by count:
61611 gmail.com 43578 yahoo.com 18942 hotmail.com 16069 aol.com 4871 sbcglobal.net 3647 msn.com 3479 comcast.net 2027 verizon.net 1722 att.net 1693 icloud.com 1693 earthlink.net 1526 cox.net 1486 bellsouth.net 1026 outlook.com 1023 me.com 970 live.com 940 charter.net 898 mac.com 887 gladney.org 879 em-boxes.net
Over 40,000 entries contained passwords, with a mix of both hashed and plaintext ones.
Over 15,000 unique SSN numbers were also present, in plaintext. This number isn’t that accurate as some passport and medicaid number entries also contained what looked like an SSN number.
After verifying that Gladney was responsible for the server, I got some contacts and sent them an email.
Notifying Gladney
On April 7th, the day I found this, I emailed the CEO, the COO, the Executive VP and the IT Supervisor of Gladney.
The same day I emailed them, the server started timing out and hasn’t allowed unauthenticated connections since.
The company did not reply to my email but I sent a follow up on April 15th asking questions regarding notifications to affected individuals and mentioned I could delay my publication in case they needed more time to send notifications.
Final Comment
As of publishing this, the company has not replied back to any of my emails but I will update this post if that changes.
If you’re interested in more incidents I dealt with, you can check all my public finds indexed by country on the post below: