Server from University Tec.mx exposed publicly
Tecnológico de Monterrey had a server with 160,000 personal files from student and attendees, related to Semana i event, exposed publicly.
Who is Tecnológico de Monterrey?
“Monterrey Institute of Technology and Higher Education, also known as Technological Institute of Monterrey or just Tec, is a private research university based in Monterrey, Mexico” according to their Wikipedia page.
Finding the exposed data
At the end of November 2024 while looking at my private feed for exposed servers with PII to flag, I noticed a server with Mexican data exposed such as health insurance and INE cards, but I couldn’t easily identify whoever was responsible for the server so I just flagged it to check later.
A couple weeks later I got back to this server to take a better look and also saw the server also contained a lot of pictures of student cards from Tecnológico de Monterrey and with some other information I saw on the server I found out the server was related to an event of sorts that the University has every year called Semana i. Most of the data exposed on the server seemed to relate to personal documents from attendees of the event and was from multiple years, some of it dating as back as 2018.
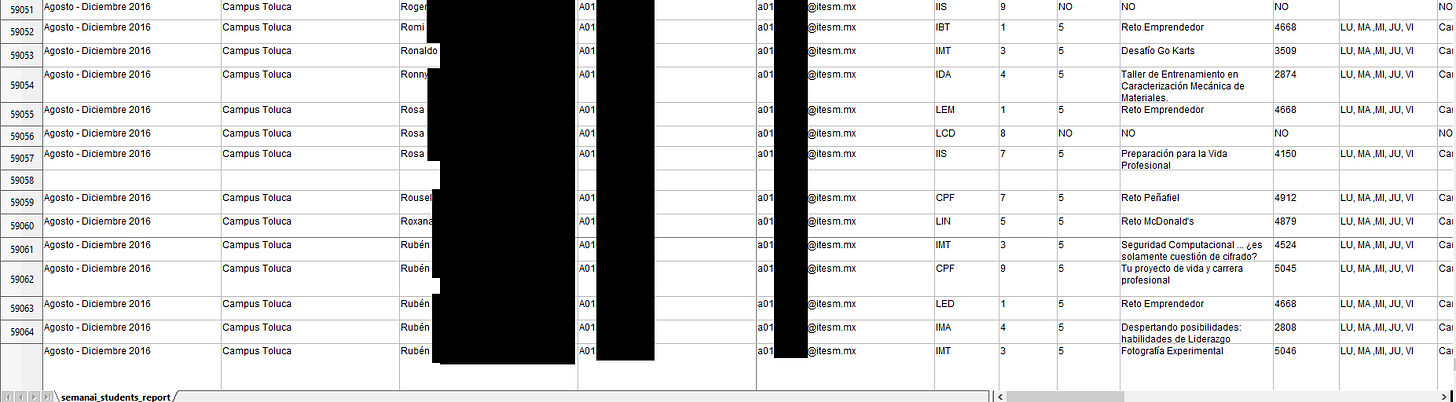
File count: 161,042 Size: 105.24GB
The personal documents were split between almost 130,000 sub directories so I couldn’t tell how many people had their data exposed. Most directories only had 1 file inside and those included:
Health insurance cards INE cards Medical certificates Liability wavers for Semana i with emergency contact data Tec de Monterrey student cards Proof of payment (Transaction screenshots)



The data was mostly from Mexican people but not exclusively. I saw PII from multiple other countries such Chile, Spain and the United States.
There were also a couple thousand spreadsheets, multiple per day of the event, with Tec de Monterrey students information such as the Campus they were enlisted at, their full name, enrollment ID, university email and notes such as enrolled activities or reason for dismissal. I do not know how many students total listed on this spreadsheets but one I checked had over 59,000 entries and the data on the spreadsheets seemed to be from 2016 to 2023 according to filenames.
I also checked my general logs to see the first time this server was flagged as exposed and the first time was around mid 2021 but it was for a different volume and I only flagged the volume with the data I’m talking about on this post years later, on October 21st 2024.
First attempt at notifying the University
Disclaimer: Half of the emails I tried, over multiple incidents, listed on the CSIRT website below don’t even work, the ones that did never replied back to me so I have no clue if they ever did something or not. The one email that “replied” to me was from Mexican gov and they wanted me to provide a phone number to read their automated replies through Websafe email so I don’t know what they said either. I wouldn’t be able to recommend one email from that list to use for help based on my previous attempts.
Now, I’ve dealt with a few things in Mexico recently and in one of those cases I had a couple of people commenting that I should try to use emails listed here: https://csirt.com.mx when trying to get help closing servers down, so that’s what I did on this and multiple others cases recently even though it went as bad as I expected.
On December 16th 2024 I sent an email to tecservices@servicios.tec.mx from a ProtonMail account and sent a DM to their X account @TecdeMonterrey. I got an automated reply to my DM but nothing else.
A few days after no reply to my email I started wondering if the domain was blocked, I’ve had this issue multiple times in the past, so on December 19th 2024 I sent another email, this time, from a Gmail account and CC’d 2 emails from the CSIRT list that I thought would fit the criteria for this specific incident: csirt@cudi.edu.mx and incidentes@cert.unam.mx. The email to cert.unam.mx was not delivered.
The day after I sent the email from Gmail I got an email on my Proton inbox saying my initial email had expired without any moderator decision, I did not get the same message regarding the email sent from Gmail so I assume they got that one but either ignored it or didn’t actually read what I sent.
I do not think anything was done related to this notifications or if it was then the message was not delivered to the right people, I’ll explain why next.
Getting internal help to close the server
On December 21st by pure coincidence I noticed a Professor from the University actually started following me recently because of another post I did related to Mexican data:
I sent him a message asking if he could get me any email I could contact to help close down the server and he replied that it could take a bit to get a contact but he was working on it and would let me know, which I already expected as this was pretty close to the holidays.
On January 9th 2025 he got back to me and provided me a contact from someone at the International Relations department and after a few days of being blocked again, changing email provider and some DMs, the message was forwarded to the IT security team and on January 14th 2025 the data exposure was finally fixed.
Final notes
I have not seen the volume I talked about here listed on any of the websites I have access to that scan this type of services, so I can’t say for sure if this was found by others or not. I can’t also say for how long this was exposed for, if it was exposed back in 2021 or earlier, or if it was exposed later on. Only whoever has access to the server logs, if they exist, would be able to answer those questions.
Yet another example of me having to resort to personal connections and internal company emails to get things solved because the publicly listed contacts do not work at all. This is a common occurrence when I’m dealing with issues and it’s one of the reasons my list of pending reports is as big as the published ones, sometimes I can’t find anyone to care enough about it.
Thanks to both people at the University who helped me close this down.
If you’re interested in more incidents I dealt with, you can check all my public finds indexed by country on the post below: