Putting out virtual fires in Germany
A community effort to close down potentially 400 exposed servers from Fire Departments around Germany.
Update from November 19th:
I’ve been contacted by a few Fire Departments asking me to verify if their data was exposed on this, from what I’ve been told most of this departments were told they weren’t affected. 5 out of 5 I was contacted about and checked were affected. I’m not releasing my list as I know 100% the list isn’t complete and I don’t want to give the company a list to base of and ignore everyone else I didn’t find, it is more than likely that if you used Fireplan software and people uploaded files/pictures to it, your data was exposed and probably for a long time too.Update from November 25th: I decided to write a more detailed post with additional information that you can check here:
Oh an exposed server, oh look another, wait... It’s actually hundreds of them!
The amount of exposed data and servers out there is so big that usually when I find a server with exposed PII but there is only a small amount of files inside, unless I immediately know who to contact I just skip it because simply there wouldn’t be enough time available in my lifetime to try and contact all these people not to mention most people don’t even bother reading my emails when I do contact them.
On October 16th while looking at some of my logs I started noticing a lot of German PII, mainly drivers licences and “selfies” (owner holding the card) with people in firefighter uniforms, the first one or two I checked only listed a few hundred files total so I didn’t pay much attention to it at first, but I kept seeing more and more of the same style of pictures all hosted on different servers so this peaked my interest and I went digging.
I instantly spotted that all the servers I was looking at followed the same naming pattern for server + files and all included a German town in the naming scheme.
I searched online for a list of a couple thousand town names and within a couple of minutes I had a list of 180+ exposed servers that matched the patterns. I manually verified over 90 of them to see if the data was related and then looked for contacts in Germany that could help close this.
I also checked my logs for the first time I flagged any server related to this and I can see this was exposed at least since February 2024.
Examining what I found
Between the 180+ servers I flagged were over 130,000 files, the biggest server had around 11,000 exposed files, some had public listing enabled but were empty. The total amount of servers is higher than this but I don’t have access to the full list of servers hosted related to this.
The files inside included:
- Drivers Licences - Selfies of people holding their licences - Selfies of people at the Fire Stations (from kids to elderly people) - Medical Attestations - Training certificates
There were other types of documents inside some of the servers, too many for me to ID as I don’t understand German and it’s time consuming to ID them. Not every server contained the same type of files, it would depend on what each fire station would upload to it.



The search for help fixing the exposure
I initially emailed poststelle@bfdi.bund.de and poststelle@lda.bayern.de on the same day I found this (October 16th) as those were the emails I initially found online related to Data Protection in Germany.
On the 21st after not hearing back from anyone on this I made a post asking for possible contacts that could help close this down.
People suggested a lot of possible avenues to contact but I decided to try email CERT-Bund and go from there. Not long after I sent the email, someone from the Baden-Württemberg Data Protection Authority reached out to me through DMs offering to help out. I forwarded the email with the information and it turned out coincidentally that a lot of the servers belonged to Fire Departments in Baden-Württemberg.
The next day the company responsible for the software related to the servers was contacted and public access was removed.
The connection between the servers
All the servers were linked to https://www.fireplan.de, owners of a fire department software “Full-featured management software including supporting alarm functions. Practical and everything from a single source.” that, according to their FAQ, you simply need to install and have internet access to use, they take care of the rest.
On their website they mention the software is running on around 400 fire departments, I don’t know if every single one was exposed, only the company could confirm that, but from what I looked at, this looked like every server was setup the same way so it’s possible they were all running the same misconfig.
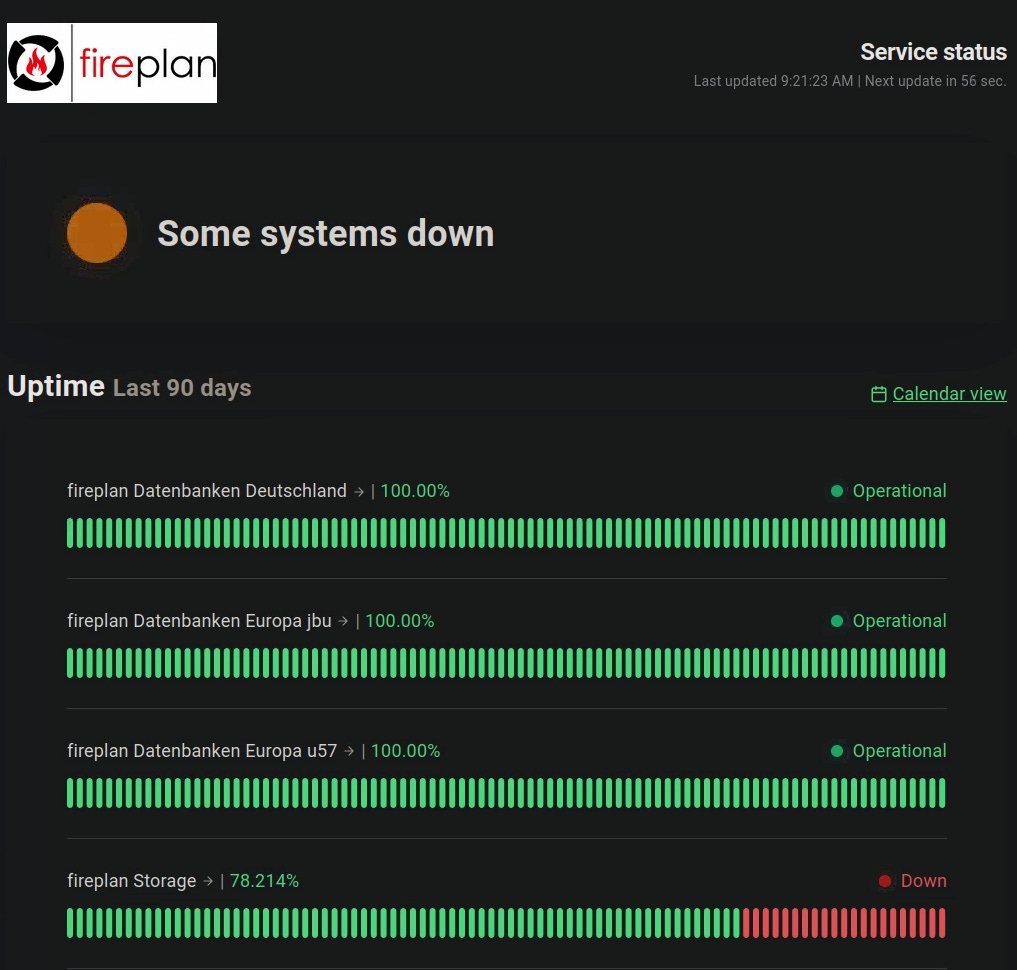
From the day this got closed to the day of posting this, the software status page shows the Storage part of it is offline, I can’t confirm if it is indeed offline or just showing the wrong status though.
Acknowledgments and Thanks
First of all thanks to everyone who interacted with my original post asking for help regarding this, so many people reached out either publicly or privately and tried to help, great to know the community is there when needed.
Also a special thanks to Baden-Württemberg Data Protection Authority (@lfdi) and more specifically Alvar Freude (@alvar) for reaching out through DMs and helping out verifying and contacting the company responsible for the software. I've dealt with a lot of different companies, gov agencies, certs and it's not often you get someone as open and helpful. From the fast action taken to close this to the updates and replies to inquires I had, I have nothing but praise for the great job done.
Final Notes
As said before, the first time I flagged any server related to this was in February 2024, the exposure probably dates back further than that, but only the company would be able to tell exactly how long and if they had logs, how many people accessed the data.
This affected hundreds of Fire Departments across multiple states, I’m not listing any specifically but the company lists some of their clients here.
I do not know if or when a public disclosure will come out of this as that’s not my job to decide and I’ve not been in contact with anyone from the company.