LCPTracker.com (LCPTracker Inc.)
Over 8.7TB, 44 million US documents related to payrolls exposed publicly, millions of SSN
Who is LCPTracker?
“LCPtracker, Inc. is the leading solution for certified payroll reporting software, construction site compliance management, and workforce reporting.” according to LCPTracker.com website
Finding the exposed data
This server initially showed up on my logs without authentication to list or download files on July 12th, I was busy with my personal life so I only started looking at the logs on August 14th.
It took over 12 hours just to grab the URLs alone before I even started looking at what was exposed in this.
When I started checking the documents exposed in here I almost instantly knew I would have to try and ID whoever it was that owned this as I was seeing a lot of payrolls from the US with PII in them, full SSN included.
I tried looking at the folders on the server to see if I could spot any clues but it got me even more intrigued, as I kept seeing GOV agencies as folder names, so I started going through documents to try and get to the owners of the server.
It took me hours of looking at random documents since I had no idea about the existence of LCPTracker at first, but I eventually found a legal document that pointed to them and the rest of what I was looking at started to make sense. I googled a couple of the GOV agencies I was seeing and LCPTracker together and I saw the partnerships between them so I started looking at emails to contact.
Examining what was exposed
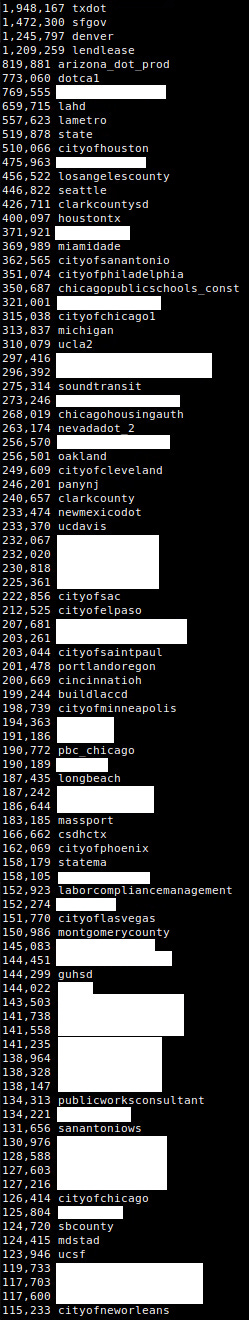
Each company had it’s own folder so through the links I calculated how many documents were exposed for each of them.
The server contained 1344 folders, some clients contained a couple of folders so I can’t exactly tell how many companies were in here and I also won’t release a full list as I don’t want to expose a lot of LCPTracker clients that might not be as public as gov entities.
The total amount of files exposed when I listed this server was: 44,390,147 (8.72TB)
The 44 million file question
What were all this documents? I can’t confirm every type of document exposed due to the amount of them, and I only looked at a small sample. The exposed files varied from client to client but what I can confirm is:
- Millions of weekly CPR(Certified Payroll Reports) - The documents contained full name, address, SSN, employee ID, phone number, ethnicity and gender and hourly rates as well as work type and location. It also contained contractor and project information. The fields that were filled would depend on the company. Ex: Some TxDOT CPR files have full name, employee ID and hourly rate while the SFgov files I checked have full name, address, employee ID, full SSN, hourly rate, gender and ethnicity. - Millions of weekly NPCPR(Certified Payroll Reports for Non Performing Week). This didn’t contain employee PII but project and contractor information. - Daily logs for projects, employee names and classifications, equipment on site and hours and description of the work done that day. - DAS 140 and 142 forms - Empty template forms for multiple companies that could be used to make forged documents



First attempt at notification
On August 16th I sent an email to support@, contact@, privacy@, 2 CEO emails and a Director. The CEO and Director emails instantly bounced back saying “Access denied.”
Second attempt at notification
On August 20th with no reply and the server still exposed I again emailed the previous emails plus security@, after a couple of hours with no reply and kinda expecting the same outcome of the first attempt of notification, I contacted 2 of their clients, Texas and California Department of Transport.
Another couple hours passed and I got 2 emails at the exact same minute.
CA DOT asked me how I determined the documents related to them, which I answered.
LCPTracker Chief Legal Officer was the other email.
Around 3 hours later I got another email from the CLO thanking me again, informing me that they’ve remediated some of the problems and were in the process of quickly fixing the rest of it and would keep me updated. He also asked if he could speak with me and if I had a contact number to call.
Since I’d rather not give my private phone for any company to freely call me whenever they want, I told him I’d prefer communications stay through email, but I’d be happy to reply to any questions he might have through email ( the server was still exposed at this point as well ) and I didn’t get any more updates or replies until I emailed the company over a month later on September 25th asking for an update on this. I also provided them with my Signal in case they wanted to talk with me after all.
The company replied to me a couple of hours later saying they were working with third party specialists and law enforcement to investigate this issue and would update me whenever the investigation was complete and their clients were given the full scope of it.
And so I waited and waited… until today
Earlier today I was on a call with someone who was aware of this incident and I was commenting that I should probably ask for another update somewhere after new years and then my infosec live feed updated and I read “LCPTracker reports data breach”.

I was waiting for an update for the last 2 months, the update never came but since the company disclosed this, I finished writing the post that I have been holding for the last 3 months.
Company Disclosure
The company sent disclosure notifications on November 22nd you can check the full notification here: Link
Final notes
The company never asked me any IPs I used (I have no clue now either, I might be able to tell if x or y IP might of been me but that’s about it) or what files I accessed. I also don’t know what their investigation came up to.
I can say though, this cloud server did not come from any public feed and it’s possible no one else found this, I can’t be sure about that though, I have very little information about the company side of this incident.