Internal chat database for multiple US companies exposed publicly
Millions of chat messages and over 130,000 attachments exposing PII and PHI were public for over a month.
On February 1st 2025 while looking at some exposed databases I noticed one for what looked like an internal chat for employees.
Over two-thirds of the 308 users on the chat were for Savantcare, a Mental and Behaviour Health Clinic from the United States, and around 30 users were from OVLG (Oak View Law Group).
By looking at the rest of the entries on the user table I noticed the chat was likely setup by Grmtech, a Digital Marketing and SEO company from India.
The domain linked to the IP address hosting the database was http://mortgagefit.com which is another client of Grmtech.
It’s likely other clients of Grmtech also had user accounts for the chat, the ones mentioned are just the ones that related to most of the information exposed.
The exposed data
The database contained over 130,000 exposed files that may have been attachments sent through the chat.
Some of what I saw included:
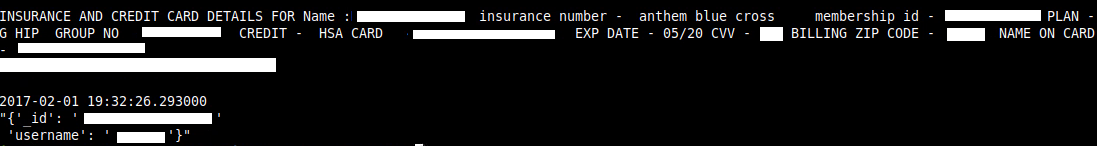
CURES reports(Controlled Substance Utilization Review and Evaluation System), patient medical reports, patient registration forms related to ZocDoc check-ins, professional liability insurance certs, lab reports, insurance medication reviews, insurance cards, ROI(release of information) docs, recorded calls, resumes and more.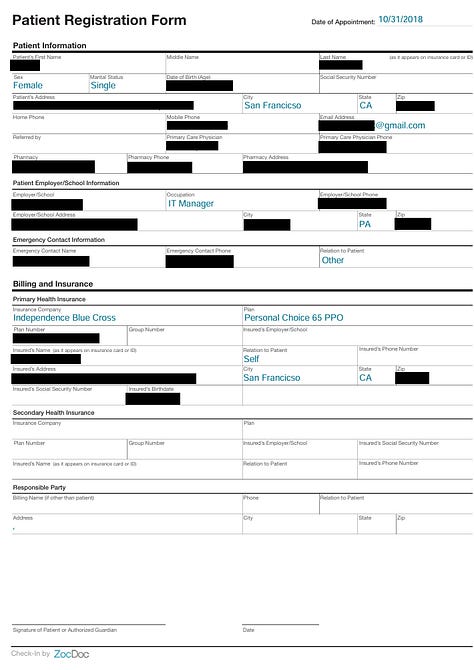
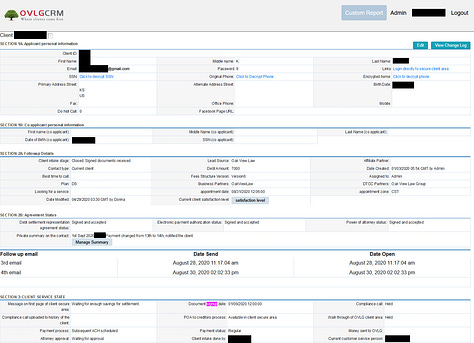

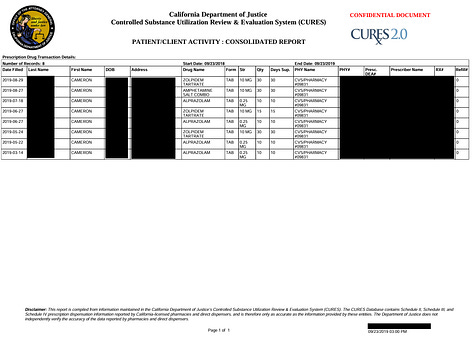

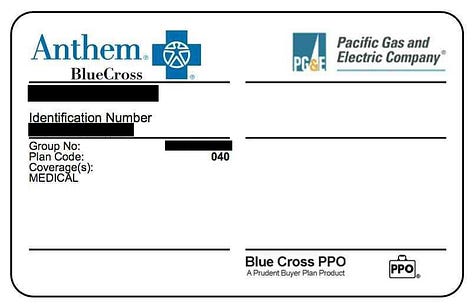
The database also contained over 6 million chat messages, some of them were exposing more PII/PHI.
Around 1.8 million messages contained references to ‘Savantcare’ so I decided to contact the company directly.
Alerting Savantcare and Grmtech
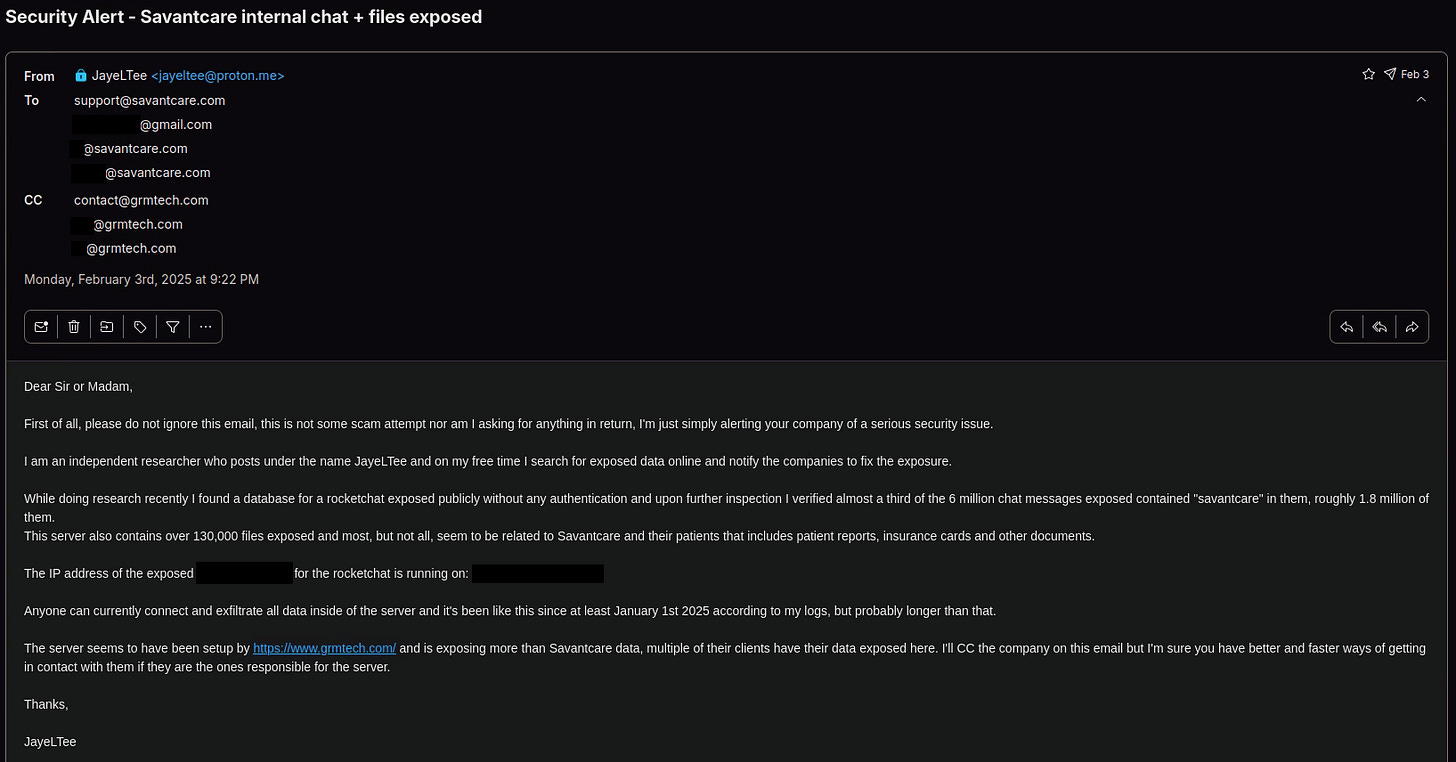
On February 3rd I sent an email to Savantcare explaining the issue with the internal chat they were using and also mentioned that I noticed Grmtech seemed to be the company responsible for the chat and that I would be cc’ing them.
I also pointed out that Savantcare probably had better ways to reach out to them.
Since one of the emails I added was support@, a help desk ticket was opened with Savantcare.
The day after I sent the email the help desk ticket got closed and I was asked how they did.
The server was still exposed at this point, so I replied saying everything was still the same and I did not undertand why they closed the ticket without doing anything.
Some hours later, on February 4th, the server wasn’t connecting anymore and just timed out.
I have no idea if Savantcare contacted Grmtech about it or if anyone from Grmtech had actually read my emails and fixed the issue.
Final Comments
I checked my logs to see the first time I flagged this database as being publicly exposed and the first entry is from January 1st 2025.
I don’t know if Grmtech notified any of the companies that used the chat about their data being publicly exposed for over a month.
The situation is the same about whether Savantcare notified any of the employees and patients either as I never got a reply to my email or the help desk ticket.